TLDR
K8s clusters are not by default accessible by outside network
Ingress lets securely access clusters from outside
Ingress Resource is a set of rules
Ingress Controller implements these rules
Intro
Although Pods within a Kubernetes cluster can readily communicate with one another, they are not by default open to traffic from outside networks.
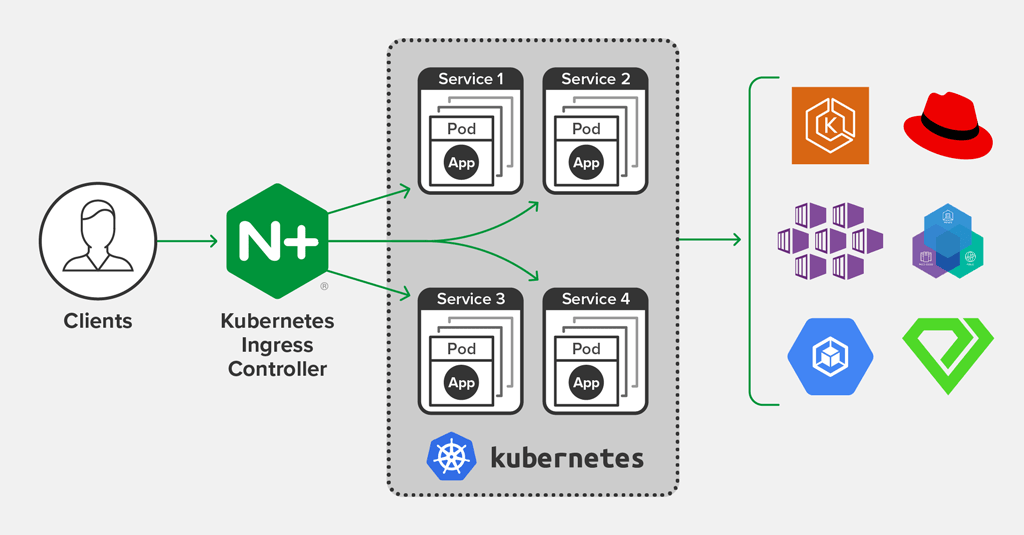
(NGINX, 2020)
Some Terminologies to understand ingress
Kubernetes API: used by users to communicate with the clusters
ClusterIP: adds internal endpoints for in-cluster communication
NodePort: exposes a static port on each of the Nodes to route external calls to internal services
LoadBalancer: creates an external load balancer to route external requests to internal services
Ingress Resource vs Ingress Controller
Strictly speaking, an Ingress is an API object that defines the traffic routing rules (e.g. load balancing, SSL termination, path-based routing, protocol), whereas the Ingress Controller is the component responsible for fulfilling those requests. (Hwang, 2020)
A Kubernetes Ingress Resource is an API object that demonstrates how internet traffic from Kubernetes cluster internal Services that submit requests to collections of Pods should be routed. The Ingress has no power by itself. The user can specify how external clients are forwarded to a cluster’s internal Services by sending a configuration request to the ingress controller.
The identity of an ingress controller within a cluster need not be known to the user. Any Kubernetes Cluster using any ingress controller will produce the same outcome for the same Ingress resource.
To put it another way, the cluster’s layer 7 traffic routing for HTTP/HTTPS requests is established by Kubernetes Ingresses. They also provide a tonne of extra features. For instance, Ingresses enable the definition of the TLS configuration for TLS termination.
Ingress Security
RBAC
Kubernetes Role-Based Access Control (RBAC) is a form of identity and access management (IAM) that involves a set of permissions or template that determines who (subjects) can execute what (verbs), where (namespaces). (Redhat.com, 2022)
A Kubernetes cluster contains a variety of namespaces. Being able to provide access to only the parts a user needs is essential for the security of an application. RBAC gives more visibility and decreased blast radius in case of a security issue by guaranteeing authorized users access to limited resources.
Just-In-Time Provision (JIT)
A Service Account is a temporarily active account, with limited permissions, assigned to an authenticated user. The resources allowed will be determined by the user’s role (RBAC) and limited time by the Service Account. Hence the term “Just-In-Time” Provision.
Certificates and Privacy Keys
The Ingress controller handles SSL, whereas the TLS certificate references are added to the Ingress resource as a Kubernetes secret object, which is accessed by the Ingress controller and made a part of its configuration.
Both SSL and TLS, also known as Transport Layer Security and Secure Socket Layers, are cryptographic protocols that encrypt data and verify a connection as it is transferred over the Internet.
You can check Ben Hirschberg’s blog to see how to implement these on your K8s deployment.
Read More
You can read more about Ingress, Cluster Security, List of Ingress controllers, etc. from the references below:
NGINX. (2020). Announcing NGINX Ingress Controller for Kubernetes Release 1.7.0 — NGINX. [online] Available at: https://www.nginx.com/blog/announcing-nginx-ingress-controller-for-kubernetes-release-1-7-0/ [Accessed 1 Dec. 2022].
Hwang, Y. (2020). Kubernetes Ingress Controller Overview & Comparison | The Startup. [online] Medium. Available at: https://medium.com/swlh/kubernetes-ingress-controller-overview-81abbaca19ec [Accessed 1 Dec. 2022].
NGINX. (2022). What Is an Ingress Controller? — NGINX. [online] Available at: https://www.nginx.com/resources/glossary/kubernetes-ingress-controller/ [Accessed 1 Dec. 2022].
Mikula, K. (2022). What is a Kubernetes Ingress Controller | Traefik Labs. [online] Traefik Labs: Makes Networking Boring. Available at: https://traefik.io/glossary/kubernetes-ingress-and-ingress-controller-101/#:~:text=An%20ingress%20controller%20acts%20as,Pods%20running%20inside%20the%20platform. [Accessed 1 Dec. 2022].
Mikula, K. (2022). What is a Kubernetes Ingress Controller | Traefik Labs. [online] Traefik Labs: Makes Networking Boring. Available at: https://traefik.io/glossary/kubernetes-ingress-and-ingress-controller-101/#:~:text=An%20ingress%20controller%20acts%20as,Pods%20running%20inside%20the%20platform. [Accessed 1 Dec. 2022].
Palark.com. (2019). Comparing Ingress controllers for Kubernetes. [online] Available at: https://blog.palark.com/comparing-ingress-controllers-for-kubernetes/ [Accessed 1 Dec. 2022].
Hirschberg, B. (2022). How to secure Kubernetes ingress? | ARMO. [online] ARMO. Available at: https://www.armosec.io/blog/kubernetes-ingress-security/ [Accessed 1 Dec. 2022].
Spacelift. (2022). Kubernetes Security : 5 Best Practices for 4C Security Model. [online] Available at: https://spacelift.io/blog/kubernetes-security [Accessed 3 Jan. 2023].

Click -> HERE <- to connect with me!